Too Many Adverts and pop-ups in your Web Browser Maybe your Router has been Hijacked
If you’ve recently found Too Many Adverts and pop-ups in your Web Browser and your plagued by pornographic pop-ups and irritating adverts, there might be a simple – but dangerous – explanation.
Too Many Adverts and pop-ups in your Web Browser
Maybe hackers have hijacked your internet router?
Security researchers at Ara Labs have warned of an active campaign which has seen attackers changing DNS settings on routers, causing unauthorised ads and adult content to appear on virtually all websites affected users visit, generating income for the attackers.
DNS records work like a telephone book, converting human-readable website names like tripwire.com or google.com into a sequence of numbers understandable by the internet. A problem occurs, however, if someone manages to change the lookup – so when your browser tries to reach google.com it is really taken to a different website entirely.
One way to do this is for an attack to break into your internet router (perhaps because you are using the default security settings, or have an easy-to-crack password, or because you have not kept it patched against security vulnerabilities) and meddle with its DNS settings.
Too Many Adverts and pop-ups in your Web Browser
When one of these router DNS hijacks are successful, the DNS settings on the router are changed to point to a rogue DNS server controlled by the attackers. By default, most common operating systems (Windows, OS X, iOS, Android, Ubuntu) are configured to automatically retrieve their DNS settings from the router when they connect to a network (via DHCP). This means that when a device connects to a compromised router’s network it will be automatically configured to use the same rogue DNS settings as router.
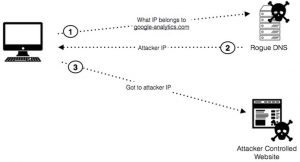
If an attacker controls the DNS server that you are using to lookup an IP they can substitute the correct IP for the IP of a server that is under their control. Then you might connect to this IP thinking that you are connecting to a certain domain when in fact you are connecting to a server controlled by the attacker.
It’s easy to imagine such a technique being deployed to dupe users into believing that they are visiting online genuine banking websites, but Ara Labs is reporting that this latest attack is exploiting the fact that so many websites on the internet run a Google Analytics script to measure and track visitor traffic.
The rogue DNS server responds to requests to access google-analytics.com with a bogus IP address, tricking browsers into running code which is under the attackers’ control.
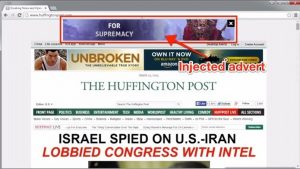
In other words, you can visit an entirely legitimate and innocent website only to find that it is now peppered with additional adverts, helping the hackers earn income through affiliate schemes. In addition, the adverts displayed might be for content which the site would not normally think appropriate – such as adult webcam sites and pornographic content.
None of that is the website owners’ fault, but chances are that you would think that they were responsible – and not realise that your router has been hijacked.
A video produced by Ara Labs demonstrated the malware injecting adverts onto popular websites such as the Huffington Post and the New York Times.
The injected code could, of course, just as easily contain a malicious exploit kit designed to infect visiting computers with malware by taking advantage of, say, an Adobe Flash vulnerability.
The fact of the matter is that the hackers now have control, and are able to do what they want with the code they can run on virtually all of the websites you are likely to visit.
Your best defence? Make sure that you have kept your router’s firmware properly patched with the latest updates, and never stick with the default login credentials provided when you first purchased the device.